In: NFC
January 8th, 2020
Smartphone Hacking coming to your phone now

There’s a lot of stories in the media at the moment in light of revelations that certain government agencies can hack into your smartphone.
Whether it’s for spying on you for audio bits, capturing visual bits by turning your camera on without you ever knowing or just tracking your where abouts, it seems Smartphone hacking is hitting the mainstream.
Criminals have been looking for ways to exploit smartphones since they were invented way back when Steve Jobs released the first generation iPhone® on June 29th 2007.
Fast forward almost ten years and how our lives have changed because of that “light bulb” moment from Apple. Every year at the hackers convention Def Con held in Las Vegas these hackers are show casing how easy these technologies we use daily are open and vulnerable to hacking.
Find out how Armourcell™ can protect your Android phone
![]() The interesting thing is that most people who have ever used “Find My” feature for a lost phone, laptop etc is tapping into a form of surveillance. Whether it’s a partner tracking a spouse’s movements or downloading malicious code hidden in an app your kids just to downloaded to somebody walking past you in the street injecting malicious code via the backdoor through the NFC (Near Field Communication) or tap and go / bump feature located on most smartphones these days.
The interesting thing is that most people who have ever used “Find My” feature for a lost phone, laptop etc is tapping into a form of surveillance. Whether it’s a partner tracking a spouse’s movements or downloading malicious code hidden in an app your kids just to downloaded to somebody walking past you in the street injecting malicious code via the backdoor through the NFC (Near Field Communication) or tap and go / bump feature located on most smartphones these days.
The fact is with so much information on our smartphones its just way to tempting to not be exploited by criminals and let’s just say certain “agencies”.
As smartphone owners, we need to start stepping up security measures and that starts with simple things like two-stage pin security code, knowing what you’re downloading is from a reliable source, checking permissions of the apps your downloading etc.
 The harder thing to monitor is walk-by NFC injections, this is when somebody injects a malicious code into your phone via the NFC feature that tells your phone to do something (like next time your in a wifi zone, your phone is fooled to back up, then boots up a browser in the background to a malicious web address that copies all your files to the server) Scary stuff and everything & I mean everything is worth money on the dark web or deep web.
The harder thing to monitor is walk-by NFC injections, this is when somebody injects a malicious code into your phone via the NFC feature that tells your phone to do something (like next time your in a wifi zone, your phone is fooled to back up, then boots up a browser in the background to a malicious web address that copies all your files to the server) Scary stuff and everything & I mean everything is worth money on the dark web or deep web.
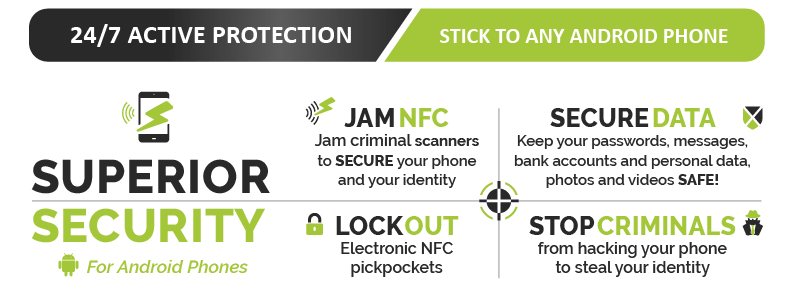
At Armourcard™ we knew this vulnerability was coming and that’s why we developed our latest product called Armourcell™ which utilises our patented micro jamming technology found in our original Armourcard product and applies it to your Android smartphone.
Armourcell™ effectively shuts the NFC backdoor into your phone and also stops your phone acting as a sniffer via the NFC feature for credit card data out in the open.
To find out more about Armourcell™ for Android phones here
August 2nd, 2017
The Australian Newspaper features Armourcard CEO Tyler Harris

 Our CEO Tyler Harris has been featured in the national newspaper The Australian both in print and online on the 1st Aug 2017 in an Article called
Our CEO Tyler Harris has been featured in the national newspaper The Australian both in print and online on the 1st Aug 2017 in an Article called
Armourcard ads to the Arsenal
Mr Harris talked about the next battleground for identity theft and data stolen is on your smartphone and how criminals are exploiting the back door into your phone to get your data.
 Harris went on to say
Harris went on to say
As Australians rely on smartphones to go about their personal and professional transactions, data stored on those devices is the new gold.
and continued
What many people don’t realise is that mobile phones can be penetrated through the NFC technology which is constantly on and emitting a signal. All it takes is for malicious code to be injected through the NFC feature on a smartphone and a hacker pushing out malicious RFID signal to a phone by the RFID chip, to get hold of passwords, photographs, and other personal information.
 Tyler introduced Armourcell, our latest product to protect your android smartphone from this type of attack
Tyler introduced Armourcell, our latest product to protect your android smartphone from this type of attack
With Armourcell, we are providing smartphone users peace of mind and protecting their data from being compromised,
Mr Harris said.
To read the full article please go to The Australian
Find out more about how Armourcell can protect your phone

Australian Financial Review reports on identity theft in the digital age
Tyler Harris the CEO of Armourcard was interviewed for comments by Duncan Hughes the highly respected journalist from the Australian Financial Review on Identity theft and whats coming our way.

You may also like to read about how over 400 mil is wirelessly skimmed from Australians by electronic pickpockets
Find out how you can protect your smartphone with Armourcell

Contact-less technology adoption in Australia is exceeding expectations
Australia has long been a testing ground for new technologies and products just like contact-less technology found in credit cards & ePassports, the isolation of the continent in relation to North America & Europe probably contributes to the notion of a testing ground that can give real insights into the future global roll-out of products (plus they can contain any issues before they become global issues). An example of this (let me digress for a moment to prove the point), is the automotive industry here in Australia, we have more marks or manufactures in this country than in the USA or Europe.
ABARTH, ALFA ROMEO, ASTON MARTIN, AUSTIN, ACURA
BEDFORD, BENTLEY, BOLWELL, BUFORI,
CADILLAC, CATERHAM, CHERY, CHEVROLET, CHRYSLER, CITROEN
DAEWOO, DAIHATSU, DODGE
FIAT, FORD
GEELY,GREAT WALL
HINO,HUMMER, HOLDEN (GM) HYUNDAI, HONDA
INFINITI, ISUZU
JAGUAR, JEEP
KIA
LAND ROVER, LEXUS, LOTUS
MINI, MITSUBISHI
OPEL
PORSCHE, PROTON
RANGE ROVER, RENAULT
SAAB, SKODA, SSANGYONG, SUBARU, SUZUKI
TATA
VOLVO, VW
Just to name a few manufactures & given some of the marks have come and gone with this disparity of variety to population base (as of writing this post an estimated 23,547,811 people in Australia according to the Bureau of statistics) also proves that many global companies see Australia as a great & containable testing ground.
Part of the reason for this is many Australians often fall into the category of ”early adopter” meaning they don’t mind giving it a go. This is especially is relevant in early technology up-takes.
This is why Australia has been one of the first countries to fully embrace the contact-less payment systems that started fully rolling out in Australia in 2009 and partially before this date. Well before many countries.
Even in these early adverts it show how easy it is to quickly use this facility to check-out, however it seems they may have reduced the read distance for the readers as now you have to actually hold the card a little longer than the footage shows. Perhaps because people were a little freaked out when their card was read from a greater distance unintendedly.
In recent research undertaken by RFintelligence who are a global provider of business intelligence focusing exclusively on financial services, shows that Australians are leading the way with adopting this technology into their lives, which would be a great result for the card issuing companies & financial institutions.
RFi’s latest payments research shows the take-up of contactless payments is gathering pace. By March 2014 two-thirds of Australian adults had a contactless card, up from 26 per cent in September 2011. And according to RFi, the activation rate, or the proportion of contactless card owners who have used their card to make a contactless payment, has increased, from 45 per cent to 72 per cent in the same period.
One of the points I’d like to bring up is when you get issued a new card here in Australia you do not get the option to ‘op-out’ of a RFID enabled cards like visa’s PayWave & mastercards PayPass^ you just get sent them so I guess I can understand the increase in the stat’s & lets be honest the ‘tap & go’ facility is kind of convenient to use so I can also attest to the uptake of the use of the ‘contact-less’ check-out terminals as well. Hell we use them.
 What many of these people who have these cards in their wallet or purse do not know is that very same technology that is used in these cards & RFID check-out readers can also be used to wirelessly skim your cards & personal data. It is the nature of this technology, RFID transmits your data over open airwaves.
What many of these people who have these cards in their wallet or purse do not know is that very same technology that is used in these cards & RFID check-out readers can also be used to wirelessly skim your cards & personal data. It is the nature of this technology, RFID transmits your data over open airwaves.
The early origins of this RFID technology lay in the cold war and was originally used as a spy tool. Now, this technology is used everywhere from inventory tracking (yes a tracking tool) to embedded in your pets or into your clothes. If you’re interested in how governments, companies & institutions want to you use this technology on you, then you should read this book called SPYCHIPS by Dr Katherine Albrecht who is the a global expert and champion of protecting your?privacy and exposing the truth & motives behind companies & governments wanting to implement this RFID technology. A truly interesting read.
Now we are not saying the convenience of this technology is not great nor are we saying that the financial institutions & governments who have implemented this technology are not trying to better secure it, what we are saying is we personally were not satisfied with the level of protection offered by the passive protective devices on the market that claim to supposedly protect your data from being wirelessly skimmed.
That is why we developed the world 1st Active RFID & NFC protective device called Armourcard, we do not try and block or shield RFID signals (passive) this method has varying degrees of success & often at most may simply reduce the distance you could be skimmed, but might not stop it.*
Armourcard ‘Actively’ powers up with its own battery (not relying on convection from the RFID reader) and emits a jamming forcefield that actually jams the most common frequency these contact-less devices communicate over of 13.56 MHz.
Find out why Armourcard is better here
We know there are a lot of different RFID protective devices on the market like RFID blocking wallets or shielding credit card sleeves that are passive, we developed Armourcard to personally protect our own data as we were concerned with the global roll-out of this technology and the limitations of passive protection offered in the marketplace.
If you want to protect your personal information from wireless skimming then Armourcard with its Active jamming technology is the superior choice.
BUY ARMOURCARD NOW
Source:
^Please note: Visa payWave, Mastercard PayPass & American Express ExpressPay are all registered trademarks of the afore mentioned relevant card issuing companies, These companies do not sponsor or officially endorse this website, Armourcard is independent & just protects these cards from being skimmed. *Passive Shields or metallic wallets Only reduce the signal strength, this will not block a high-powered RFID reader Source: Credit Card Fraud The contactless Generation | Kristin Paget | Chief Hacker, Recursion Ventures. Please note Kristin Paget does not sponsor or officially endorse this website or product, we have only referenced a report that is freely available online to download and read. All credit for the report and its findings go to Kristin Paget.
October 23rd, 2013
40% of smartphone users still unaware of identity theft threats

Smartphone users still unaware of identity theft threats
Four in ten (40%) smartphone users in the United States agree that they don’t understand cybersecurity well enough to know how to protect themselves, according to LifeLock.
The online survey, conducted in August by Harris Interactive, asked more than 2,000 smartphone users about their smartphone security habits and assessed their knowledge of and participation in potentially risky behaviour.
Many smartphone users reported sharing data that can leave them susceptible to identity theft and other identity fraud dangers. Users are engaging in several compromising behaviours that may leave them at risk to fraudulent activity:
- 44% of smartphone users have a personal banking or finance app on their smartphone.
- 35% of those who have a social networking app on their smartphone allow the app to know the GPS location of their phone when downloading the app.
- 36% of those surveyed have not utilized protection such as a PIN, tracking software, and/or remote wiping capabilities for their smartphone.
It’s clear that the majority of those surveyed don’t take simple steps to secure their devices,? said Neil Chase, Vice President of Education with LifeLock. ?And it varies with age. The survey found that people ages 18-34 are significantly more likely to use the same password for every app than those who are 35-54, and people 55 and over are even more careful.
Despite the prevalence of identity theft, users don’t see their smartphones as the biggest risk. Seventy-one per cent of users agrees that losing their wallet is a bigger risk for identity theft than losing a smartphone. Further, 36% of participants believe they are more likely to have their car stolen than their identity stolen. However, based on an annual survey published by Javelin Strategy & Research, identity fraud affected 12.6 million adult consumers in 2012, while, according to the FBI, fewer than one million cars were stolen in 2012.
LifeLock recommends the following actions to secure a smartphone:
Protect the device with a strong password. Do not use a date of birth or banking PIN as a password.
Do not allow downloaded apps to access GPS location.
Ensure all apps use different usernames and passwords.
Wipe all personal information from the device before replacing or upgrading.
ARMOURCARD also recommends the following actions to secure a smartphone:
If your phone is NFC (Near Field Communication) enabled to be sure to watch what apps you download as if a Trojan is embedded in a ‘FREE app’ that activates your NFC your smartphone could become a remote credit card skimmer.
To protect yourself you can use Armourcard alongside your phone and it will jam the NFC signal.
Buy ARMOURCARD now
July 3rd, 2013
Rogue Smartphone Apps to skim your Credit Card Data.

APPetite for destruction, Apps that can Skim your credit card data
Not long ago I wrote a blog post on the new wave of smartphones that are NFC enabled that can use free apps to skim credit cards and the potential threat that anyone with a NFC enabled phone can potentially skim your credit cards. So protecting your credit cards from electronic pickpockets in this new age of NFC enabled phones just got a little bit more necessary.
 Now you have to think about every APP you download.
Now you have to think about every APP you download.
Because every APP could hold a Trojan program inside that runs in the background and basically searches via your NFC enabled smartphone for credit cards details.
The credit cards that use the RFID chip like Visa cards PayWave, MasterCard PayPass or American Express’s ExpresPay.
So next time you drop your phone inside your handbag or by your wallet watch out it may be your skimmers best friend.
Your phone with the rogue App installed will locate the RFID enabled cards, interrogate them for their data and secretly email those credit card numbers to a criminal 3rd party without you ever knowing it.
Pretty scary stuff isn’t it.
Well, the only way to protect yourself truly is to put an ARMOURCARD inside your wallet alongside all your RFID enabled credit / debit cards.
ARMOURCARD’s patented ACTIVE RFID & NFC protection actually jams all RFID & NFC signals running on the most common bandwidth for contact-less devices of 13.56Mhz.
So even if you have a rogue APP there is NO chance it could get your credit card data, ARMOURCARD would instantly power up when the APP would try and communicate with the cards and jam the signals.
 Isn’t it time you started to protect your own identity and data!
Isn’t it time you started to protect your own identity and data!
Walt, one of our US competitors is again on the PR trail and showing just how easy it is these days with trojan APPs.
We think Walt does a great job getting the message out there, so thanks, Walt.
We just don’t believe that passive RFID blocking wallets or shielding sleeves (like what Walt stocks) are the best way for protecting your data.
In-fact there are many reports by industries top hacking security experts* stating that these passive blocking wallets and sleeves at the very BEST may limit the distance too which a reader can read your cards but mostly if a reader is dialled up in power and antenna strength these passive RFID blocking wallets and sleeves WILL BE penetrated.
The choice is yours it’s your personal data, we chose active protection that is why we developed ARMOURCARD.
Get Protected Today BUY ARMOURCARD NOW!
Source^ Passive Shields or metallic wallets Only reduce the signal strength, this will not block a high-powered RFID reader Source: Credit Card Fraud The contactless Generation | Kristin Paget | Chief Hacker, Recursion Ventures. – See more at: https://armourcard.com/rfid-blocking/
June 12th, 2013
The Australian Newspaper Article on electronic pickpocketing

The Australian Newspaper runs a story on the new wave of electronic pickpocketing coming to a wallet near you.
In the weekend version of ‘The Australian’ newspaper (8.6.13), two reporters Adam Shand & Ben Westcott report on how electronic pickpocketing is now a real concern.
We applaud Adam, Ben and The Australian Newspaper for bringing this to the attention of the general public.
Now as we have reported in a previous ARMOURCARD blog post, there are now FREE apps that allow you to skim card data with your Near Field Enabled (NFC) smartphones. These include the Samsung Galaxy 3 or Galaxy 4, latest Windows phones and rumors are that the next generation of iPhone will also be NFC enabled. What that means to you and I is everyone with a smartphone potentially will be able to use that phone to electronically pickpocket your data without you even knowing it.
We did our own bench testing
At ARMOURCARD we don’t claim to be experts in hacking or skimming.? However we were able to download a range of apps that were capable of extracting card data and applied them to testing. We found that the apps were able to extract different data from a range of cards some even including the cardholders name . The point being that if a couple of novices could easily obtain the equipment and means to do this, what would a seasoned professional be capable of accomplishing? We were not comfortable with the ease at which our personal data could be compromised. ARMOURCARD provides the first electronic solution to this vulnerability.
What do the card issuers say:
In the article a spokes person for Visa, Judy Shaw, said that it was:
“technically possible to lift some details from its cards using NFC scanning technology”
In the article it was said that “the level of security was extremely high and contact-less payments were as safe as traditional cards”. Traditional cards do not have a history of being secure. The size of the fraud industry which has emerged from the lack of card security is living testament to this. Why else would financial institutions limit? transactions to under $100 if there was no cause for concern?? Does that sound secure to you?
If you are wanting to secure your identity today, then get ‘active RFID & NFC protection from ARMOURCARD.
Why risk your identity? Buy ARMOURCARD today!
To view the full article click on the image below.
June 4th, 2013
Privacy champion explains electronic pickpocketting

Global privacy champion Dr Katherine Albrecht talks about the next wave of RFID crime.
Dr Katherine Albrecht has been the champion of outing the RFID industries plans to track every purchase and track you via RFID for over 10 years.
I have recently connected with Katherine and I am sending her an ARMOURCARD.
Hopefully once Katherine sees how effective our ‘Active RFID & NFC Protection’ technology is she will also say to her following that now there is an effective solution to the vulnerabilities surrounding this contact-less technology that is? in-use today and not just advise requesting a non RFID enabled card from your banks.
With ARMOURCARD’s technology, you actually get the best of both worlds.
Firstly, you get security from being skimmed this way as we jam RFID & NFC signals so no RFID reader can interrogate your cards,
Secondly, you get the convenience to use these contact-less payment terminals. We have incorporated a capacity switch on every ARMOURCARD which enables you to temporarily turn of ARMOURCARD’s jamming so you can still get the convenience of being able to use ‘tap&go’ payment terminals.
Find out more what makes ARMOURCARD the best solution here
If you are interested in Katherine’s book called ‘Spychips’ you can purchase it through Amazon here or through the Amazon widget located on the left side of the page.
May 10th, 2013
RFID a Spy Tool part 1

Radio-frequency identification (RFID) as a Spy tool of the future
A quick definition:
Radio-frequency identification (RFID) is the use of a wireless non-contact system that uses radio-frequency electromagnetic fields to transfer data from a tag attached to an object, for the purposes of automatic identification and tracking.
Put simply think of RFID as like your FM radio waves, they can penetrate walls, clothes, doors etc etc, with the right RFID reader you can trigger the interrogation of the RFID tag within your credit cards, ePassports, enhanced driver licenses, library cards etc etc. So RFID as a spy tool was how it got started.
Find out more about how RFID works here
Great Seal Bug or BUGATE – A cold war spy story
 RFID has been around since WWII and its primary function was for espionage or spying. There is a famous cold war instance whereby the KGB used this very same technology in 1945 to eavesdrop on the US Ambassador.
RFID has been around since WWII and its primary function was for espionage or spying. There is a famous cold war instance whereby the KGB used this very same technology in 1945 to eavesdrop on the US Ambassador.
The KGB used Russian school children to present a beautiful wooden carving of the seal of the United States of America to the US Ambassador Averall Harriman. He proudly displayed the plague in his embassy residential office, where it hung within earshot of America’s Cold War secrets.
The device consisted of eavesdropping apparatus that was dormant until activated by what was termed
fantastically advanced bit of applied electronics

Just like the RFID & NFC tags today, the trojan plaque’s device was powered by invisible radio waves.
It was powered up by high-frequency waves pointed from a van that was parked outside the embassy.
The beauty of this device is as did not require a battery to work and if the radio waves were not directed at it, the device lay dormant, so detection was very hard if not actively transmitting.
Hence why it took 6 years to discover it.
To discover more about how vulnerable you are with your RFID / NFC enabled cards / epassports etc go here
Buy ARMOURCARD now and get protected from this type of electronic spying