By: Armourcard Team
November 18th, 2021
Win the Ultimate Safety & Security Bundle

THE COMPETITION HAS ENDED, WINNER HAS BEEN SELECTED.
If you would like to be notified of any future competitions please sign-up for our newsletter (at the bottom of the page in the footer) or follow us on Facebook
October 30th, 2021
What you need to know about ‘Juice Jacking’ to stay protected

Summary:
-
Juice Jacking is a real security threat and an official US warning has gone out warning people to avoid public charging stations
-
Criminals can access your data or install malware via a public charging station
-
Stay safe by either using a power outlet or stop data transfer by adding a DataBLOCK between the charging station and your device

Unless you have managed to avoid any news or media outlets in the last while you have no doubt heard the term “juice jacking”. So let’s start with the basics – what is it? Wikipedia offers the following definition:
“Juice jacking is a type of cyber attack involving a charging port that doubles as a data connection, typically over USB. This often involves either installing malware or surreptitiously copying sensitive data from a smart phone, tablet, or other computer device.”
Why is this something you need to know about? Think about the last time you visited a hospital, café or airport lounge. You may have noticed public charging stations. These charging stations have saved me many times when I have been about to run out of battery and need to keep my laptop or phone alive. Powerpoints are just never there when you need them. Unfortunately, these saviours of modern life are now the target for criminals. The attack uses a charging port or infected cable to exfiltrate data from the connected device or upload malware onto it. The term was first used by Brian Krebs in 2011 after a proof of concept was conducted at DEF CON by Wall of Sheep. When users plugged their phones into a free charging station, a message appeared on the kiosk screen saying:
“You should not trust public kiosks with your smart phone. Information can be retrieved or downloaded without your consent. Luckily for you, this station has taken the ethical route and your data is safe. Enjoy the free charge!”
Like scammers who steal debit card numbers by putting illegal card-reading devices, or skimmers, on A.T.M.s, hackers can easily rip out USB ports and replace them with their own malicious hardware, said Vyas Sekar, a professor at CyLab, a security and privacy research institute at Carnegie Mellon University.
“It’s easy to modify the outlet if the attacker has physical access,” Professor Sekar said.
Even a 60-second power-up can be enough to compromise your phone’s data. This is because USB cables allow the transmission of both power and data streams simultaneously. Victims can be left vulnerable to identity theft, financial fraud, and significant stress.
“People want the convenience of charging their phones and tablets wherever they go,” Professor Sekar said, adding, “Obviously I would like it too, but there is a risk.”
Professor Sekar said consumers could also use attachable protective devices on USB cables known as “USB condoms.”
“What they do is a very simple trick,” he said. “They essentially disable the data pin on the USB charger.” This means that the device will charge, but the cable will be unable to send or receive data.
The security threat is so real the Los Angeles District Attorney’s Office issued an advisory to travelers in November 2019 warning them of the potential dangers of using public USB ports.
Malwarebytes Labs explains in more detail how this works:
As you may have noticed, when you charge your phone through the USB port of your computer or laptop, this also opens up the option to move files back and forth between the two systems. That’s because a USB port is not simply a power socket. A regular USB connector has five pins, where only one is needed to charge the receiving end. Two of the others are used by default for data transfers.

USB Connection table courtesy of Sunrom
Unless you have made changes in your settings, the data transfer mode is disabled by default, except on devices running older Android versions. The connection is only visible on the end that provides the power, which in the case of juice jacking is typically not the device owner. That means, anytime a user connects to a USB port for a charge, they could also be opening up a pathway to move data between devices—a capability threat actors could abuse to steal data or install malware.
There are two ways juice jacking could work:
-
Data theft: During the charge, data is stolen from the connected device.
-
Malware installation: As soon as the connection is established, malware is dropped on the connected device. The malware remains on the device until it is detected and removed by the user.
So how can you tell if you’ve been juice jacked?
Hacked mobile devices will often go undetected. But there are a few telltale signs that your device may have been hacked. These include:
- apps taking a long time to load or frequently crashing
- excessive heating
- An unexpected drain on your battery could indicate a malicious app is now running in the background
- the device running slow or restarting without notice
- updates to device settings that you did not make
- increased or abnormal data usage.
So what is the solution?
If you are keen on the convenience of a charging station and want to avoid being attacked the simplest way is to use a power point or use a USB Data Blocker such as DataBLOCK or DataBLOCK 3 in 1. Described by Professor Sekar as a “USB condom”, the technology in these products prevents accidental data exchange when your device is plugged into someone else’s computer or a public charging station. This is achieved by blocking the data pins on a USB cable and allowing only power to flow through. This minimises the opportunities to steal your data or install malware on your mobile device. They are inexpensive and small, so very easy to carry with you.

August 10th, 2021
What is a skimming attack?

What is a skimming attack?
Skimming is an illegal practice used by identity thieves to capture credit card information from a cardholder surreptitiously. In the Australian Fraud Statistics 2019-2020 this form of crime is on the rise big time.
Why do I need to be concerned about being a victim of a skimming attack?
In our digital age, skimming has become a growing problem. Criminals can use your skimmed details to clone a new card, make online purchases or sell to other criminals. Don’t fall victim to a skimming attack, at Armourcard we have your back covered.
I don’t need to worry, the banks will simply refund the amount from the skimming attack, no drama… right?
Unfortunately, in reality, it is a painful process to deal with when your credit cards details are stolen. Whilst most banks are improving their functions around catching potentially fraudulent transactions the process to remedy is long, and painful. It is good practice to check your credit card statements on a monthly basis and not rely on the bank to catch everything. Keep an eye out for very small withdrawals such as $0.01 or $1.00 or from other countries. Fraudulent charges can continue for months.
Your compromised credit card will be canceled while investigations are carried out. You will receive your new card in the mail. This step can take longer than any of us would like. Some banks ask you to allow two weeks for this process. Yes, you read that correctly. Two. Weeks. If the account is a debit account, it will likely be frozen while investigations are carried out. It is a good idea to get a copy of your credit report to see how much damage has been done.
So you have your new card, we’re able to prove the transactions were fraudulent, and the sun is shining again, right? Well, apart from those direct debits you have set up. You will need to contact every single company and update your card details. With any luck, your bank will send you the list to update. If you forget to update a direct debit you may find you end up with late fees. Now that’s a pain.
The latest statistics* for “card not present” fraud (where your card is not physically present for the transaction, such as when the details have been stolen) are frightening. Add the ATM skimming statistics and you start to understand why there is such a focus on protecting our credit card information.

 *Source: Australian Payments Network
*Source: Australian Payments Network
So.. what is the best way to protect myself from a skimming attack and other types of fraud?
Luckily, there are some simple steps you can take to protect your data. Let’s review the basics:
- Be very cautious providing your credit card details online. Don’t click on a link from an email to make a payment. Ensure the website you are on is the one you think it is.
- Run a virus scan on your computer.
- When using an ATM give it a wiggle to check there is not a false front attached. Cover your hand when entering your PIN. Don’t share your PIN.
- Check your statements regularly – don’t rely on the banks to advise of any fraudulent activity.
- Keep your credit cards safe and secure from a skimming attack. Only take out the cards you will need and make sure you have an Armourcard next to it to prevent your data from being stolen.
- If you place your wallet in a safe box in a hotel make sure you have Armourcard RFID blocking technology protecting your cards and for passport protection look at our PassportBLOCK product All these products help protect you from a Skimming attack.
- Keep up to date with scams to avoid becoming defrauded look at official websites for up to date information like Scamwatch and follow Armourcard on Facebook for the latest updates on how to protect yourself.
- Be extremely careful when using public USB ports or charging stations as you see in airports, shopping malls, and cafes as these charging ports can be used to skim your phone or devices. This crime is called ‘Juice Jacking‘ and is on the rise. The best way to prevent your devices from being hacked when charging is to you our DataBLOCK range of products
April 2nd, 2020
COVID-19 RELATED CRIME IS ON THE RISE

COVID-19 RELATED CRIME IS ON THE RISE:
- COVID-19 has taken the world by surprise and has changed the way we live
- Many people have lost their jobs and businesses are struggling
- Unfortunately, in times like this, we see an increase in crime
- It’s more important than ever to stay safe, be vigilant online and ensure your personal data is protected from criminals when you do leave the house
- COVID-19 RELATED CRIME IS ON THE RISE
Read full article below

It is not a fun time to be reading mainstream media or listening to the news. The world as we know it has changed dramatically and we are all playing catch up. As our focus is security and helping our customers stay safe we have been playing close attention to the media reports of increased crime.
Cyber-crime is a major area of concern with those self-isolating at home online and vulnerable to scams, particularly the elderly. A further concern is criminals posing as medical practitioners requesting, and gaining, access to personal medical data. The strong message is to stay alert and protect your personal information at all times.
Here we share a few short excerpts from a broad range of media outlets:
”A laid-off worker has incentives to shift the use of time toward illicit earnings opportunities since displacements reduce legal earnings opportunities. At the same time, dismissals lessen the opportunity cost of a worker’s time during the period of unemployment.”
“The old adage that idle hands are the devil’s workshop appears to have some truth to it,” said Votruba. “This unfortunate link (to weekday crimes) highlights the importance of psychological factors–such as mental distress, self-control, financial concerns and frustration–in determining counterproductive behavior.”
#zmescience.com story coronavirus layoffs crime Dated: 16/03/2020
Hover over image to reveal more
Criminals taking advantage of coronavirus anxiety
COVID-19 fraud schemes*
- Telephone fraud – criminals call victims pretending to be clinic or hospital officials, who claim that a relative of the victim has fallen sick with the virus and request payments for medical treatment;
- Card skimming – When you do go out to get supplies ensure your ‘contactless’ credit cards are secure as criminals and opportunistic people are utilising this technology to skim your card details. This crime has become even easier for everyday people to undertake with the emergence of NFC smartphones and a host of free card reading apps found online.
- Phishing – emails claiming to be from national or global health authorities, with the aim of tricking victims to provide personal credentials or payment details, or to open an attachment containing malware.
*Interpol
^Excerpt marketwatch story
“Everyday life has essentially stopped in many countries in a bid to slow the virus, and some crimes have been declining. But reports of virus-related fraud are on the rise, along with concerns about hate crimes.”
The United Kingdom’s National Fraud Intelligence Bureau has received more than 100 reports of virus-related scams, with losses totalling more than $1.1 million (970,000 pounds).
Meanwhile, marketing schemers have quickly pivoted to offering “senior care packages” that include hand sanitizer or even a purported vaccine, which doesn’t exist. Some falsely claim that Trump has ordered that seniors get tested.
It’s all a trick to get personal information that can be used to bill federal and state health programs, health officials said.
“It’s a straight-up ruse to get your Medicare number or your Social Security number under the guise of having a test kit or a sanitary kit sent to you,” Christian Schrank, assistant inspector general for investigations at Health and Human Services.”
^marketwatch.com story coronavirus related crimes are on the rise dated: 2020-03-25
“According to a new study of 1 million laid-off Norwegians^^ over 15 years, out-of-work people commit 60% more property crimes (such as theft, shoplifting, burglary, and vandalism) in the year after losing work and have 20% more criminal charges than when employed.++”
^^ sciencedirect.com research article
So consider these questions:
- When people lose their paychecks, do they turn to crime more often?
- When people are at home more, does that deter crime?
- Will crime rates fall when police aren’t charging criminals the same way they used to?
++ poynter.org article ‘how will corona virus related closures and quarantines affect crime rates’
Armourcard International will continue to keep you updated on the latest security concerns so you are protected throughout this crisis. Don’t forget to keep your wallet protected with an Armourcard when you leave the house.
Stay Safe.
January 8th, 2020
Smartphone Hacking coming to your phone now

There’s a lot of stories in the media at the moment in light of revelations that certain government agencies can hack into your smartphone.
Whether it’s for spying on you for audio bits, capturing visual bits by turning your camera on without you ever knowing or just tracking your where abouts, it seems Smartphone hacking is hitting the mainstream.
Criminals have been looking for ways to exploit smartphones since they were invented way back when Steve Jobs released the first generation iPhone® on June 29th 2007.
Fast forward almost ten years and how our lives have changed because of that “light bulb” moment from Apple. Every year at the hackers convention Def Con held in Las Vegas these hackers are show casing how easy these technologies we use daily are open and vulnerable to hacking.
Find out how Armourcell™ can protect your Android phone
![]() The interesting thing is that most people who have ever used “Find My” feature for a lost phone, laptop etc is tapping into a form of surveillance. Whether it’s a partner tracking a spouse’s movements or downloading malicious code hidden in an app your kids just to downloaded to somebody walking past you in the street injecting malicious code via the backdoor through the NFC (Near Field Communication) or tap and go / bump feature located on most smartphones these days.
The interesting thing is that most people who have ever used “Find My” feature for a lost phone, laptop etc is tapping into a form of surveillance. Whether it’s a partner tracking a spouse’s movements or downloading malicious code hidden in an app your kids just to downloaded to somebody walking past you in the street injecting malicious code via the backdoor through the NFC (Near Field Communication) or tap and go / bump feature located on most smartphones these days.
The fact is with so much information on our smartphones its just way to tempting to not be exploited by criminals and let’s just say certain “agencies”.
As smartphone owners, we need to start stepping up security measures and that starts with simple things like two-stage pin security code, knowing what you’re downloading is from a reliable source, checking permissions of the apps your downloading etc.
 The harder thing to monitor is walk-by NFC injections, this is when somebody injects a malicious code into your phone via the NFC feature that tells your phone to do something (like next time your in a wifi zone, your phone is fooled to back up, then boots up a browser in the background to a malicious web address that copies all your files to the server) Scary stuff and everything & I mean everything is worth money on the dark web or deep web.
The harder thing to monitor is walk-by NFC injections, this is when somebody injects a malicious code into your phone via the NFC feature that tells your phone to do something (like next time your in a wifi zone, your phone is fooled to back up, then boots up a browser in the background to a malicious web address that copies all your files to the server) Scary stuff and everything & I mean everything is worth money on the dark web or deep web.
At Armourcard™ we knew this vulnerability was coming and that’s why we developed our latest product called Armourcell™ which utilises our patented micro jamming technology found in our original Armourcard product and applies it to your Android smartphone.
Armourcell™ effectively shuts the NFC backdoor into your phone and also stops your phone acting as a sniffer via the NFC feature for credit card data out in the open.
To find out more about Armourcell™ for Android phones here
July 2nd, 2019
Top 10 ways to protect yourself from identity theft

Protect yourself from identity theft
What are the best ways to prevent identity theft?
Here are 10 top tips to help protect yourself from identity theft
At ARMOURCARD we are often asked what can I do to minimise the risk of my personal data being compromised.
So we have compiled a list of the 10 top ways to protect yourself. (for the detailed list go here)
-
Shred it – like you mean too
-
Stash it – keep your receipts when out then shred it when home
-
Lock it up – mailboxes, filing cabinets, phones
-
Financial diligence – check your statements and all correspondence
-
Protect it – ePickpocketing
-
Check-ups – keep up to date credit checks
-
Red Flags – look out for any unusual activity
-
Freeze it – install a freeze on your credit
-
Opt-out – of pre-approved credit offers
-
Password Savvy – use different passwords
It’s often easy to forget just how easy your identity can be stolen especially in the technical age in-which we are living. By taking several steps and making them routine you will help greatly reduce your chances of having your identity stolen.
To find more about what each one of the 10 Tips means and how you can implement it go here
April 4th, 2019
5 Best tips to protect you from ATM skimming

5 BEST tips to protect you from ATM skimming
In light of the spate of ATM scams going on here and in Bali recently, it is time to look at ways to protect yourself.
ATM skimming (or physical skimming) has been around for years in-fact ever since the birth of automatic teller machines and the roll-out in the 1980’s. Lately the criminals are getting even more advanced in there brazen perpetration of this crime, from gas pumps to store terminals and even bank ATM machines it seems the criminal will stop at nothing to get your hard earned cash.
We at Armourcard know all about many types of skimming and Armourcard protects you from RFID wireless skimming of your ‘Tap & Go’ cards. ATM skimming (Your card details being skimmed at a machine) has no real protection other than your vigilance in protecting yourself every time your withdraw money from a ATM.
Here are our 6 best tips you should do when your at a ATM machine – EVERY-TIME
1. Always pull, push, shake and rattle where you put your card in (in-fact try to remove it) gently…
2. Drum, pull or push and rattle all around the ATM to see if anything else is loose like the keypad. (you may get some strange looks but it is worth it so you don’t get skimmed)
3. Look for a camera overhead or a pin-hole camera above the key pad or even in a pamphlet holder that are sometimes attached to an ATM (directed at the keypad)
4. Always cover your hand when putting in pin. (Yes obvious we know, but you would be surprised how many people forget this basic step. (Especially when your in a rush or being distracted)
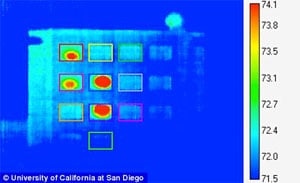 5. After you have put your pin in, place your entire hand flat over every key on the keypad to transfer heat signature. (you do this because criminals are using your heat signature left by your fingers to get your pin-number, for example, the first digit of your pin will be cooler than the last digit you put in through the colour spectrum.) so a clever way to mess that up just places your hand over the keyboard for a second or 2. (This can be done while you wait for your cash)
5. After you have put your pin in, place your entire hand flat over every key on the keypad to transfer heat signature. (you do this because criminals are using your heat signature left by your fingers to get your pin-number, for example, the first digit of your pin will be cooler than the last digit you put in through the colour spectrum.) so a clever way to mess that up just places your hand over the keyboard for a second or 2. (This can be done while you wait for your cash)
Bonus Tip
Never re-put your pin number into retrieving your ATM card out of a machine, as shown in the recent Bali scams by doing this it opens up your account again for the criminals (often within the store after you leave) to come in and empty your card. If your card gets taken then leave it in the machine they cant empty your account without the open gateway (so do not put your pin in again which opens the gateway) accept your card is lost and call your bank.
By doing this you are helping to protect yourself from the way these criminals skim at these machines whether with a camera, heat signature or devices attached to machines.
Do it every time.
August 2nd, 2017
The Australian Newspaper features Armourcard CEO Tyler Harris

 Our CEO Tyler Harris has been featured in the national newspaper The Australian both in print and online on the 1st Aug 2017 in an Article called
Our CEO Tyler Harris has been featured in the national newspaper The Australian both in print and online on the 1st Aug 2017 in an Article called
Armourcard ads to the Arsenal
Mr Harris talked about the next battleground for identity theft and data stolen is on your smartphone and how criminals are exploiting the back door into your phone to get your data.
 Harris went on to say
Harris went on to say
As Australians rely on smartphones to go about their personal and professional transactions, data stored on those devices is the new gold.
and continued
What many people don’t realise is that mobile phones can be penetrated through the NFC technology which is constantly on and emitting a signal. All it takes is for malicious code to be injected through the NFC feature on a smartphone and a hacker pushing out malicious RFID signal to a phone by the RFID chip, to get hold of passwords, photographs, and other personal information.
 Tyler introduced Armourcell, our latest product to protect your android smartphone from this type of attack
Tyler introduced Armourcell, our latest product to protect your android smartphone from this type of attack
With Armourcell, we are providing smartphone users peace of mind and protecting their data from being compromised,
Mr Harris said.
To read the full article please go to The Australian
Find out more about how Armourcell can protect your phone

Australian Financial Review reports on identity theft in the digital age
Tyler Harris the CEO of Armourcard was interviewed for comments by Duncan Hughes the highly respected journalist from the Australian Financial Review on Identity theft and whats coming our way.

You may also like to read about how over 400 mil is wirelessly skimmed from Australians by electronic pickpockets
Find out how you can protect your smartphone with Armourcell
May 19th, 2017
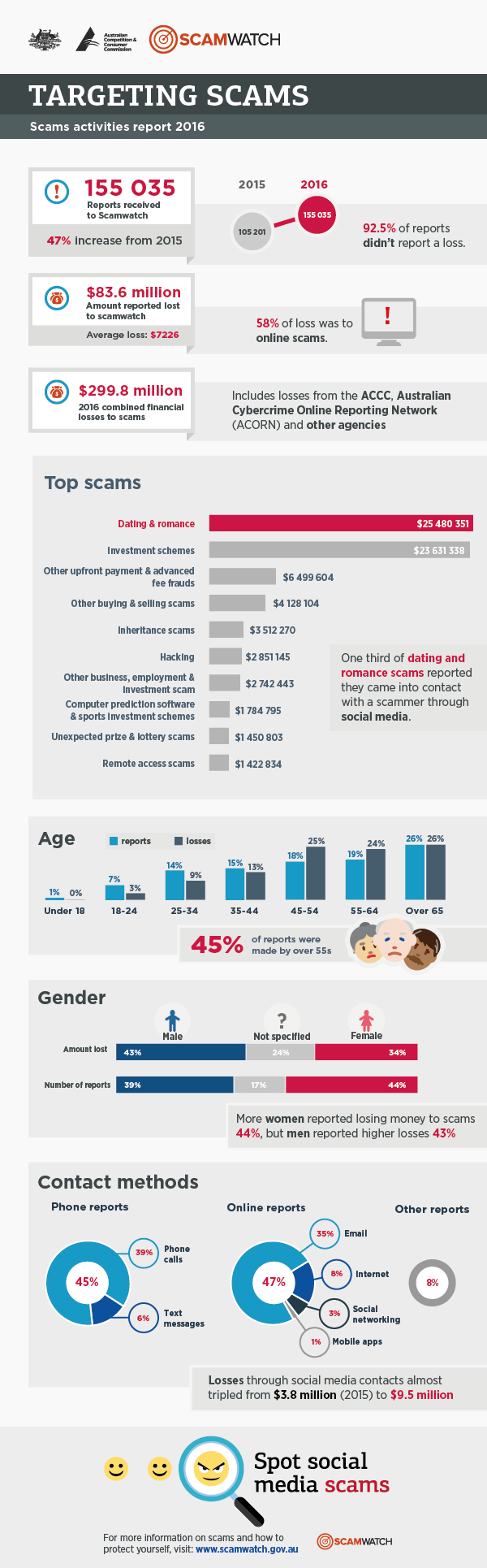
47% increase in scams reported in Australia in 2016
2016 sees a 47% increase in scams reported in Australia costing close to $300 million.
The Australian Competition and Consumer Commission’s (ACCC) annual report released today states a marked increase in scams since 2015.
Some 200,000 reports have been compiled from ACCC’s ScamWatch, Australian Cybercrime Online Reporting Network (ACCORN).
Australians over 55 accounted for 45% of the reports to ScamWatch.
Investment scams (totally $59 mil) and dating and romance scams ($42 Million) featured high on the list with social media platforms often being the launch pad for these scams.
As consumers you need to be aware and go in with open eyes, these scammers are clever and clearly pray on the vulnerable ( just by amount given to dating and romance scams) so if someone you may have become friends with on say Facebook or a dating site starts to ask you for money your alarm bells should be ringing loud and clear… run run away fast. Report it. Don’t fall for this.
The other interesting thing to watch out for is online store scams, a good rule of thumb is if the deal is to good to pass up compared to the genuine price of the goods then its properly is a scam 9 times out of 10. The product properly doesn’t even exist as the store is just front to rip you off. Before you purchase anything do some research on the business, look for ratings or reviews about the store. If you do purchase Only pay using secure payment methods such as Paypal or a credit card which often cover the fraud unto a certain amount.
The best defence against scams is education and awareness. Consumers concerned about scams should visit www.scamwatch.gov.au to keep up to date with scams to look out for, report scam activity, and get information about what to do if they become a scam victim.